iPhones are designed to protect your data, both while your device is active and when backed up to iCloud. There are multiple layers of security built into the operating system and each device comes with a passcode that locks your phone and helps prevent unauthorized access.
Security and privacy are important to you and to us. For example, when you use Touch ID to unlock your iPhone, the chances of a random person being able to guess your passcode are 1 in 50,000. And if you set up Apple Pay, your actual credit and debit card numbers are not stored on the device or on our servers.
However, since there’s always a chance that someone could figure out how to defeat our security measures, I encourage you to secure your iPhone.

Apple has designed its products to be secure by default. That covers the hardware and the software, but also what happens in between when you communicate with iCloud and Apple servers. When you use Safari, Siri, Mail, or Maps, data is encrypted with keys kept on your device or within iCloud itself.
You probably think that your iPhone can’t get malware or viruses, but this isn’t always the case. You can use iPhone malware protection to create a safe place for your company information and documents.
The best way to keep your personal information safe is to make sure you never accidentally lose your iPhone or access your iCloud account on a malicious website. It’s also wise to update the operating system software on your computer, and make sure the passwords that lock your devices are strong.
It is true that Apple has vastly improved the security of its devices with each new iteration. However, these improvements don’t mean that your gadgets are automatically immune to hacks. Apple’s mobile operating system, iOS, does not fully implement encryption and password login requirements for apps purposes.
➡ Scan, Remove and Protect iPhone from Virus and malware
Even with the system settings you have configured on the device, there are still methods hackers (even those without technical prowess) can use to access your data through questionable apps in the store or via social engineering iOS users to gain their personal log-in details.
Hackers, phishing attacks and malware are top of mind when it comes to internet security. A recent Wired article by Mat Honan, Best Mobile Apps for Protecting Your Data, had a startling statistic: 70% of iPhone users do not enable two-factor authentication. This is the number one way for securing your account and another important one is enabling a passcode lock on your device which will make sure nothing gets into your phone but you.
With the release of each new iPhone, there’s always concern about whether you should upgrade. The iPhone 12 was no different, and now with the release of the iPhone 13, there are even more questions about which model is right for you.
The best advice we can give is to be prepared and have a plan in place incase you ever find yourself in a situation where you need to resort to an emergency action. It’s not good enough anymore to just sync your phone or back it up because almost everyone has sensitive data stored on their phones. You need to insure that this data is protected and therefore, backup is just one part of protecting your iPhone in 2022.
Apple did a bang-up job of building your iPhone with a slew of enterprise-grade security features. But to take maximum advantage of these privacy and security features, you need to be aware of how they work and the best ways to use them.
Many people don’t know that there are simple best practices that, if followed, will keep you safe from identity theft, data loss, and hackers. In this Document, I recommend ways to maximize the security and privacy options on your device. The methods described in this document apply to iOS 10 and later versions of iOS.
Let’s look at five ways you can protect your iPhone, shall we?
1 Set a Strong Passcode to Protect iPhone
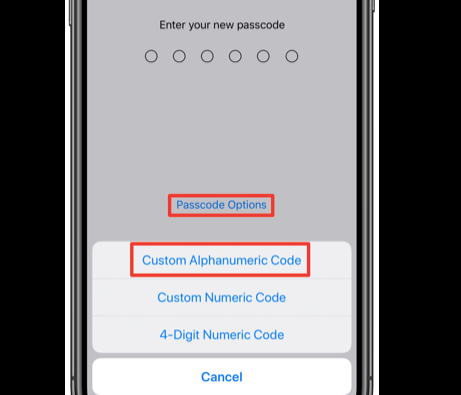
Most iPhone users don’t bother to set up a passcode on their device. Why? For starters, it’s inconvenient and time consuming. A four-digit passcode is required, and entering it is just plain annoying every time you pick up your iPhone.
One of the most important iOS security feature built into iPhone is the passcode. A passcode is made up of numbers or letters and a mix of them. This helps to protect your email accounts and app information. Not only this, it helps in keeping the content under lock & key. It’s a good idea to have an iPhone passcode even if you are not connected to the internet because certain features like accessing camera or making calls can also be enabled remotely. Setting a passcode will not protect your device in all cases but it’s one thing you can do to keep your data safe now.
As a security measure, you should set a passcode on your iPhone. A passcode is a 4-digit code that must be entered before you can use your iPhone after it has been locked by pressing the sleep/power button. You can choose to make the passcode longer than four digits if you want more protection.
2 Use Face ID or Touch ID for iPhone Protection
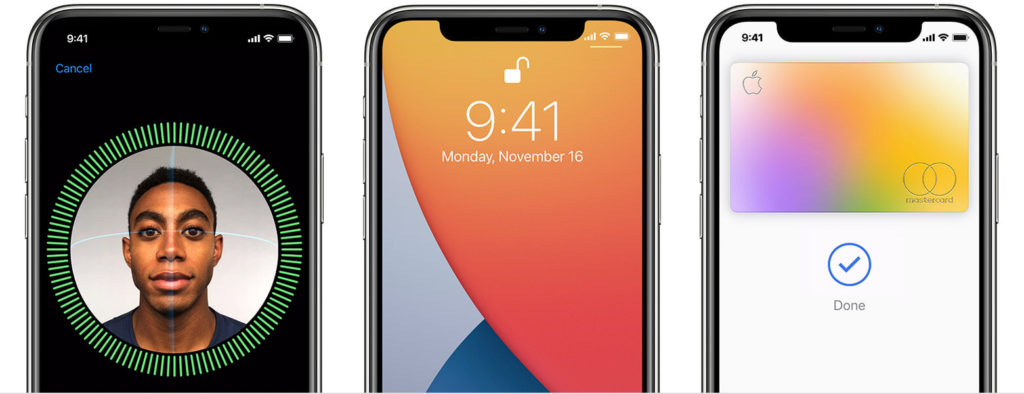
Keeping your financial and other sensitive data safe is a priority, but often our phones aren’t as secure as we’d like. So, how do you protect yourself against hackers on your iPhone? The easiest way to secure your iPhone against unauthorized access or accidental purchases is by setting up Face ID or Touch ID on your Apple device.
Face ID is the future of how you’ll unlock and use iPhone: no more Touch ID, not even with gloves on. The TrueDepth camera gives you the freedom to have a simple unlock experience while in public without having to type repeatedly on the keyboard.
When you unlock your iPhone X or later with Face ID, a mathematical model of your face is created. This model is stored in the secure enclave and never leaves your device. Face ID offers only two possible authentication methods: either a check against the securely stored mathematical model, or a challenge to re-create the model.
3 Keep Apple ID and iCloud secure
Your Apple ID provides access to your data in iCloud and your account information for services like the App Store and Apple Music on iPhone. Your Apple ID also allows others to pay for items you purchase using their credit cards, as well as send you money through the Money app.
The security of your Apple ID is important and you’re only one sign-in away from protecting your account. Apple has taken proactive measures to protect user data, but it’s still important for you to make sure your Apple ID account remains secure. Apple uses several layers of security to protect your information. One example is the 128-bit AES encryption on the session when you log in to iCloud.com or the Find my iPhone site. But you can help further protect yourself by making sure your device itself is secured. Never share your device with anyone, and don’t allow other people to use your device.
Related: Best Parental Control apps for iPhone and keep your kids and teenagers safe.
Phishing is a scam preying on trust, hope, and human error. When you receive an email or text message that claims to be from Apple and asks you to do something (like clicking a link or providing personal information like passwords), it’s a scam. Avoid it by never following links in the email: always type the address into your browser yourself. Never provide personal information to people who cold call you over the phone. They’re scammers, not Apple.
4 Turn on Find My iPhone
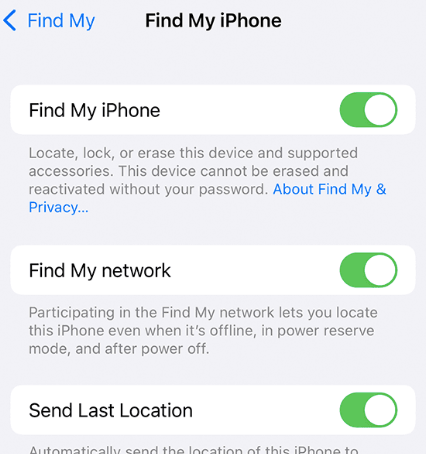
Find My iPhone helps you locate your missing iPhone, iPad, or iPod touch. It even allows you to remotely erase it. You can use Find My iPhone on iCloud.com from any computer, as well as from the Find My iPhone app on another iOS device. Your lost device needs to be on and connected to Wi‑Fi or cellular network. If you’re using iOS 7 or later, your lost device needs to have a passcode set.
Find My iPhone is an app you should enable on all of your iOS devices as soon as possible. If the battery is dying or the device is powered off, use Find My on your Mac or PC to locate it on a map, unlock it, play a sound, and notify you when it’s found.
5 Use Sign in with Apple Security feature
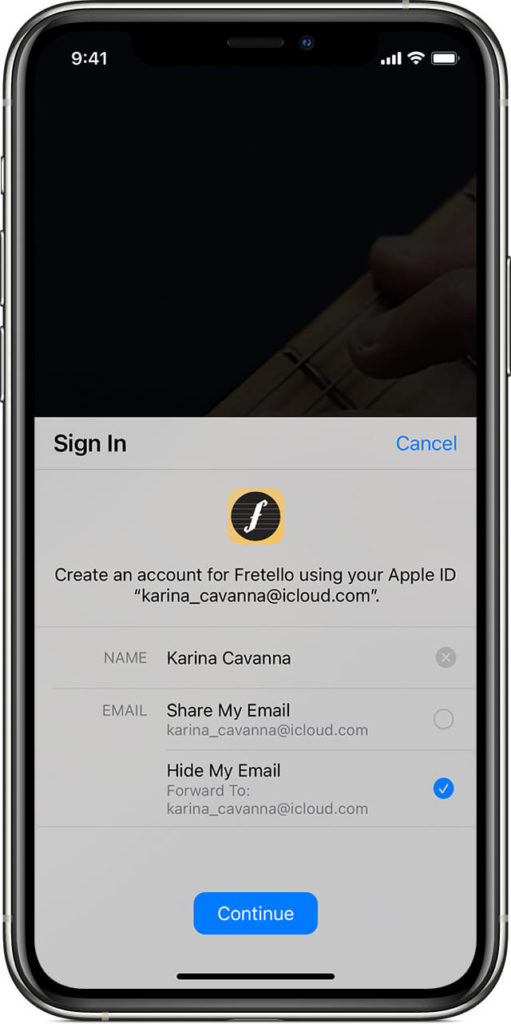
With your iPhone, iPad, or iPod touch, you can use iCloud to automatically sign in to websites and apps on your devices when you’re using Safari and other apps. To sign in using this feature, called Sign in with Apple, you need both the website or app to support it .
You don’t need a separate username or password for each website or app that supports Sign in with Apple. When you choose this option, iPhone automatically signs in with your iCloud user name and password and you don’t have to enter them again. With this option turned on, anyone who uses your device must enter your iCloud credentials (user name and password) before they can access any of the websites or apps you enabled this feature on.
6 Create a strong password for Apps and Websites
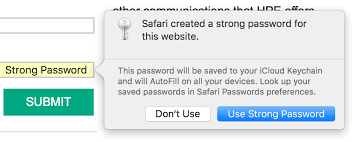
When you use the iPhone and your Apple ID to sign in to many services, such as on websites or apps, you can create a strong password that’s hard to guess. So if you have an app that doesn’t work with Sign in with Apple, this might be an option you want to try.
In fact, iPhone can create a very strong password for you, one that won’t be vulnerable to brute force attacks. A brute force attack is when an algorithm tries every possible combination of characters until it finds the right one. These mind-blowing passwords have the strength to stop hackers cold in their tracks. Brute force attacks, which are when an algorithm tries every possible combination of characters until it finds the right one, can be defended against. A brute force attack is when an algorithm tries every possible combination of characters until it finds the right one. If your password has only two possible combinations (i.e., only uses letters) and your hacker knows what those two possible combinations are — it would take the algorithm 0.0001 seconds (1/10,000th of a second) to crack your password – a timespan so small that you may not notice any lag in service or web browsing.
➡ Protect and Check Your Mac for Viruses and Malware and also check out the best antivirus available for your Mac
Effective iPhone Password: If you use a simple pattern, like “aaaaaa” or “123456”, or one of the other common passwords. An attacker (such as a skilled IT engineer) could try every possible combination until they identify the right one. If you had used four character patterns it would take approximately an hour and if you had used all the possible combinations it would take approximately 273,174 years. By mixing case, numbers and special characters for example -“AbCdEfGhIJKlMnOpQrStUvWXyz
To ensure the security of your iPhone, you may want to create strong (long and random) passwords for your frequently used accounts. In some situations, iPhone can fill in your password automatically, saving you from writing them down.
7 Use two-factor authentication
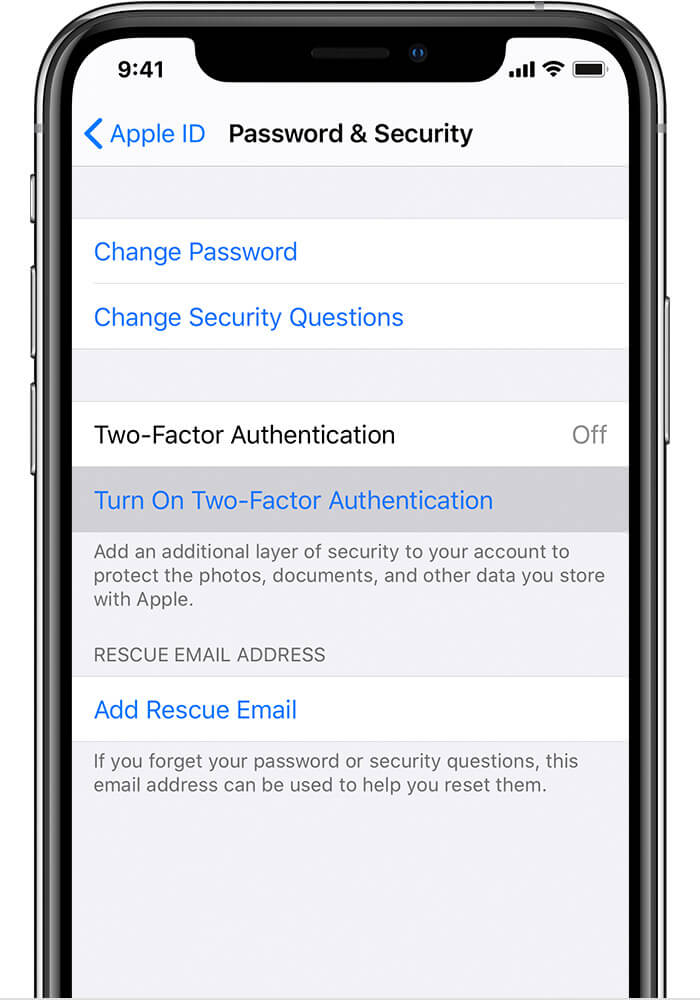
Apple’s built-in two-factor authentication makes it easy to lock down your accounts using a verification code that is generated directly on your iPhone. That code can be kept on file or distributed among two or more trusted devices. Two-factor authentication is more secure than relying on just a password, because it adds another layer of security to your account. An additional prompt sent to your phone gives you peace of mind and you can focus on what’s important – your email!
8 Review App privacy Policy
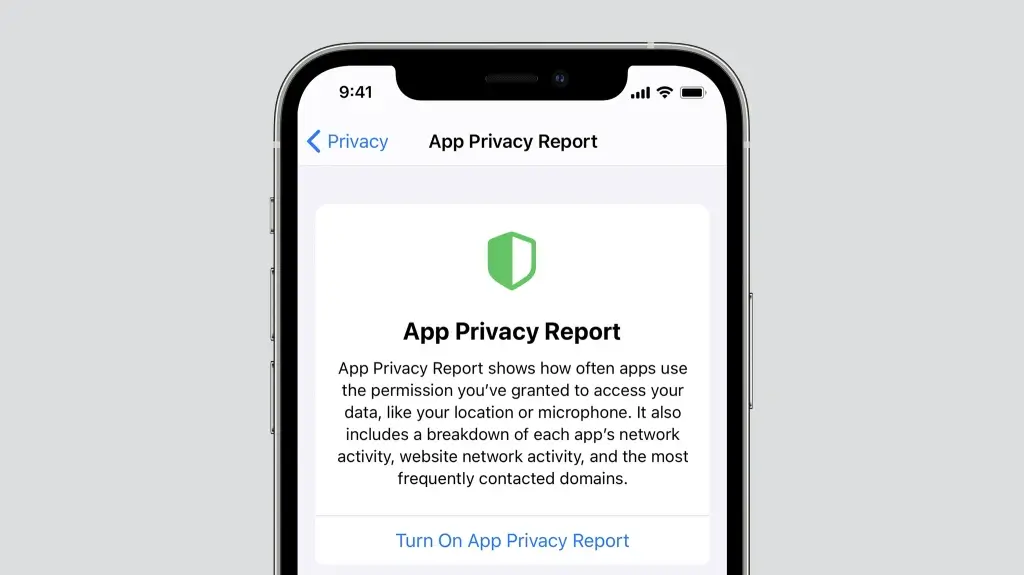
If you use apps, you may want to review the privacy practices of an app before you download it. App permissions control what personal data the app can access. See Get apps in the App Store on iPhone . For information about how your privacy is protected, review the developer’s Product Privacy Policy, which is posted on the app’s product page in the App Store.
9 Protect and Hide Mail activity
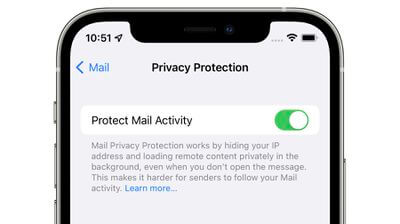
When you enable Mail Privacy Protection, certain kinds of information associated with your email account (like the IP addresses of senders and recipients) are no longer sent through Apple’s servers. Instead, Mail sends that information directly to the recipient’s Mail servers, or uses a technology called Domain Name System (DNS) or Domain Name Service (DNS), which can help prevent someone tied to a specific location from finding out your approximate location using Internet Protocol (IP) geolocation.
iCloud+ is a great iPhone and iPad feature for iCloud storage ($0.99 per month) users. If you often sign up for emails and web forms, but share your personal email address, Hide My Email is a great tool that creates unique email addresses to share instead of using your main one.
➡ Do Chromebooks need antivirus ?
This is something that I strongly recommend you turn on right away if you’re using iCloud Mail to send and receive email. Why? Attackers can use info in your email to learn more about you and use it to trick you into giving them even more information.
10 Check Malicious Trackers and Websites on Safari
Tracking software is installed on more than 500 million devices worldwide. Such software can monitor your activity and send it to a remote server. If your device is lost or stolen, malicious third parties could use this information to track and spy on you as you surf the web.
To protect you from this form of tracking, Safari can prevent websites from using certain types of cross-site tracking software. As part of its privacy-preserving Intelligent Tracking Prevention strategy, Apple reviews the browsing behaviors of hundreds of millions of customers who are signed in with their Apple ID and adapts Safari features to help Private Browsing users have an even better experience.
Open Private mode in Safari and Use shield in safari.
11 Control App tracking and Permissions
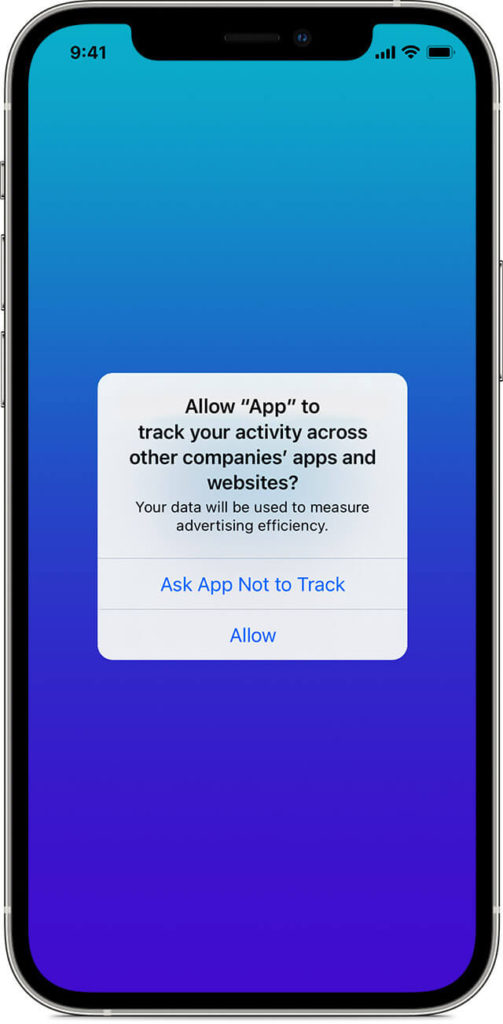
iPhone apps and online services can use information about you. Examples of this include the apps, websites and online services the iPhone connects to, such as the internet, or your employer’s network, using Bluetooth or Wi-Fi. Apps that track or use information about how you use other devices, like a Fitbit wearable device or a Samsung Smart TV, including the websites you visit on those devices, and the names of files you save to those devices while using the app on the iPhone are also part of this category.
You’ve probably read a lot of articles touting the benefits of using ad blockers, privacy & security add-ons, and VPNs to protect your online privacy. While all of these tools can help improve your online experience, but I feel that this is not enough. Using an iPhone app to track the websites that you visit, the apps you use and the amount of time you spend within each of those apps can result in an invasion of privacy (even though it does have benefits for advertisers).
You can control when and where an app can access your private data on your iPhone.
When you allow an app to track your location, it can share that information with other affiliated apps, websites, and services.
Whenever you install a new app, there’s a chance that it will want to track you using your location, your calendar, and even your contacts. This is useful if, say, you want to see which of your friends are nearby, but it’s not so great if someone else gets access to your personal info. If you’re concerned about privacy settings on apps that use your data, here’s how to add or remove location tracking permissions in iOS.
- Go to Settings > Privacy > Tracking.
- The list shows the apps that requested permission.
- You can turn permission on or off for any app on the list.
