Undoubtedly, Apple and iOS are enjoying great reputation in the market. The users are highly satisfied with their performance as they are designed to provide smooth services. However, there is still a chance to infect virus in your iPhone through various sources because of internet vulnerabilities and installed apps.

When we are using smartphone there are a lot of issues that smartphone users experience while using the phone. Many times, they experience slow processing , hanging and freezing of the phone, errors in sending text messages, poor contact performance, poor application loading and so on. These issues can be due to virus attacks. Viruses can be small or big in size.
They can be small enough to occupy less space on your mobile phone but large enough to consume all the system resources of your mobile phone and inability to work properly.
The iPhone is a great smartphone, but there’s no denying it represents a large financial investment for most people. That means there’s an entire generation with everything on those devices and an understandable desire to keep them safe from viruses.
It’s very important to stay vigilant about protecting your iOS device from malware because while they aren’t quite as prevalent in the world of iOS-based mobile devices, they’re still a serious threat to iPhones and iPads. There are multiple steps users can take to limit their exposure to viruses or other types of spyware on their iPhones.
- How to Check for Viruses on iPhone
- How to Remove Virus from iPhone / iPad
- How to secure iPhone and iPad from hackers
- How to Protect your iPhone / iPad
- Can iPhone get virus? iPhone Virus Scanner & Protection
The easiest way to remove a malware from an iPhone is to install one of the popular anti-virus software for iPhone. If you already have such software installed, check for updates and virus definitions updates as it may already have been updated to remove the latest threats. The antivirus software should run automatically once you connect your iPhone to a Wi-Fi network. While updating, ensure there are no popups on your phone screen which are preventing this update.
The malicious apps may steal your login credentials and credit card details which they can use at their will. Ensure the password protection is enabled on your device before using it publically or after leaving it unattended.
- iPhone virus can steal your personal information.
- iPhone virus can spread through the network.
- iPhone virus can drain your device battery.
- iPhone virus can make changes in your phone settings and even remove it .
- So you must know how to remove virus from iphone.
If you’ve been seeing pop-ups on your iPhone, iPad or iPod touch informing you that you have a virus and that you need to click a link to remove it then your iOS device has probably been infected with some kind of adware. These pop-ups are almost certainly caused by an adware browser extension or app installed on your device. In many cases, these pop-ups will have links that go either to a scam website or to the Apple App Store.
In some cases, they will not even link anywhere at all or just go to a general web search engine. Even if the links go to legitimate looking websites, you should still not click on them as they could be part of a phishing scam designed to steal your data.
- Do Not Jailbreak Your iPhone – Jailbreaking your iPhone is not a good idea, as it will expose you to various kinds of malware. You may be tempted to jailbreak your iPhone in order to install apps that Apple doesn’t allow in its App Store, but you should always think twice before jailbreaking your device.
- Keep Your Passwords Safe – It’s important that you use a secure password for your email account and other online accounts. Hackers can easily guess weak passwords and take over your account if you don’t have a strong password in place.
- Use Two-Factor Authentication – Two-factor authentication is another way to keep hackers at bay by requiring an additional piece of information in order for someone to log into your online accounts like Gmail or Facebook. This can be done through text messages or phone calls which makes it more difficult for hackers to access your account without permission.
- Don’t Open Links From Unknown Sources – You should never open links from unknown sources because they could lead you to malicious websites or scripts that may infect your computer with viruses or malware. If you receive an email from someone asking you to click on an email link, do not click on it unless you know exactly where it leads and why they sent it
How to get rid of a virus or malware on an iPhone and iPad
Beset with numerous viruses by hackers? Your iPhone can get infected with malware that no antivirus can protect. Don’t worry if it has happened to you. Follow these four steps to know how to remove virus from iphone.
Update iOS
If your iPhone is running on an outdated version of iOS, it may be more susceptible to attack by hackers and viruses. The best way to ensure that your device is protected against these threats is by updating the operating system.
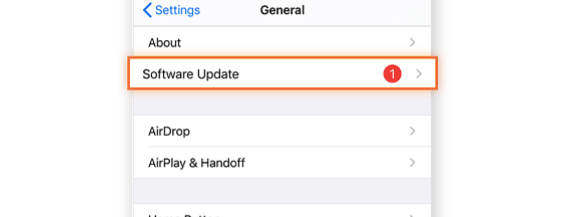
If you’ve already updated iOS, try updating again. To see if there are any updates available, open the Settings app, tap General and then Software Update.
➡ How to Update iPhone 11 / iPhone 11 Pro / iPhone 11 Pro Max
➡ How to update Safari on iPhone and iPad
If you don’t see a notification to update, go to Settings > General > Software Update and tap Download & Install.
Restart your iPhone or iPad
Restarting is a quick fix for many iphone problems. Restarting your device may help resolve issues caused by a malfunctioning third-party app or system files that have become corrupted.
Reboot your device by holding down the Sleep/Wake button until Slide to Power Off appears onscreen, then press and hold the Home button (your device will reboot). This can fix minor software glitches without losing any of your data. For example, it may resolve problems with an unresponsive screen or frozen keyboard; or with apps that won’t open, close properly or update; and even with Wi-Fi connectivity issues.
➡ Hard reset: How to Force restart iPhone 11, iPhone X, iPhone 12
Remove Unnecessary Apps
Like any computer or smartphone, iPhones can become cluttered with apps over time. Most of us keep our devices stocked with a lot of apps that we don’t need or use anymore — maybe you picked up a game years ago but never played it again, or installed an app that turned out to be worthless.
➡ How to Delete Apps on iPhone 13 Pro, 13 Pro Max
➡ How to delete apps on iPhone 11, 12, X
These are all prime targets for hackers who want access to your phone’s data or other resources like battery life. You should regularly delete any apps that you don’t need anymore so that they’re not taking up space on your device’s storage or slowing down its performance.
Clear your iPhone’s browsing history and data
If you’re a regular user of your iPhone, you may have used it to browse the internet. You may have visited websites that contained viruses or malware. These sites can infect your iPhone with a virus that can cause it to slow down or crash.
You should clear the browsing history and data on your iPhone periodically to remove any traces of these viruses.
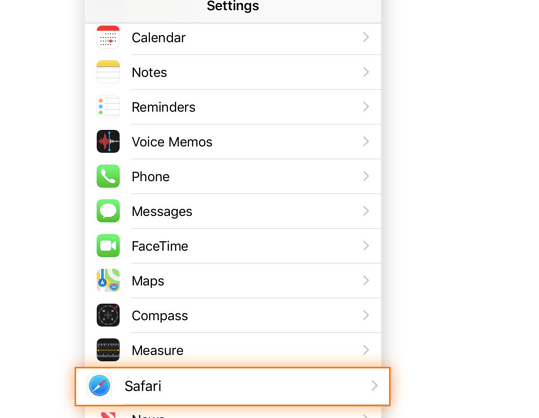
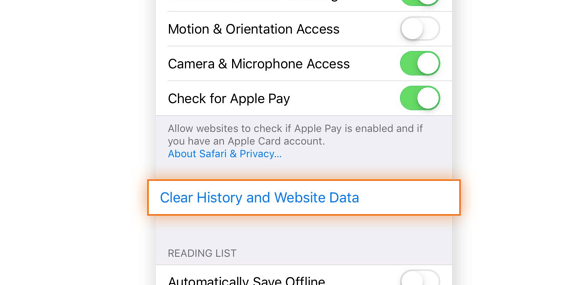
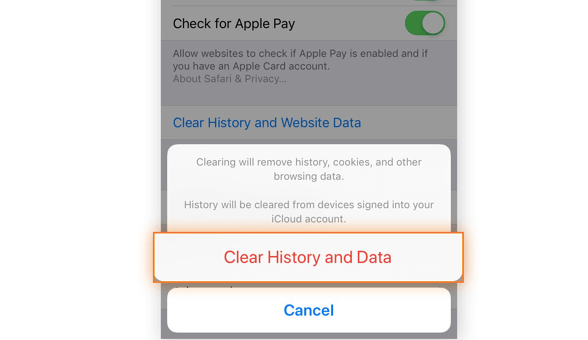
- Open the Settings app and select Safari.
- Select Clear History and Website Data.
- Tap Clear History and Data.
Restore your iPhone to a previous iCloud backup
This is the simplest method of removing a virus, as it will restore all of your files and settings back to the way they were before you got infected. You’ll need to have an iCloud account (free) and connect your iPhone to Wi-Fi on the same network as your computer before you do this.
If you don’t have a backup stored in iCloud or if you don’t have Wi-Fi access, try restoring your iPhone using iTunes instead:
Connect your iPhone to your computer via USB cable, then select it in iTunes and click on the Summary tab at the top of the screen. Scroll down until you see Restore Backup and click on it. Select the most recent backup from the list that appears, then click on Restore. The process may take some time so be patient!
➡ How to Delete Photos From iCloud
Factory reset your iPhone –
If your iPhone is running slow, or if you’re having problems with apps crashing, you may want to try resetting it. This process returns your iPhone to its original factory settings and erases all content that’s stored on it, including settings, apps and media. You’ll have to sync again after restoring your device.
If your iPhone is locked, passcode-protected or protected by Touch ID, you’ll need to enter your passcode before you can restore it. If you don’t know your passcode, contact Apple Support for help resetting your Apple ID password. If you don’t remember the password for your Apple ID account but can sign in using another method — such as with the email address associated with it — use Find My iPhone to erase all content from your device. Then try restoring again.
➡ How to Remotely Wipe an iPhone
How to check your iPhone for viruses or malware
Malware on your iPhone will cause it to behave differently than usual, making it easy to tell if your phone has an infection.
If you suspect your iPhone has a virus or malware, here’s how to check for it. These days, there are several ways you can get infected with viruses or malware on your iPhone. Here’s how to tell if your device is infected and what to do about it.
- Slow performance – Malware can drain your battery and make your device slow down, so you’ll want to look at how long it takes to launch apps, browse the Web and use other features.
- Strange app behavior – If an app is acting strangely — such as crashing or displaying ads — that could indicate a problem with the app itself or with iOS itself.
- Unexpected charges – If you see charges on your credit card bill for apps or services you didn’t authorize, that’s another sign of malware.
- Unexpected usage data usage – If you’re using more mobile data than usual, it might be due to malware that’s sucking up more data than usual.
- Unexpected pop-ups on your iPhone – These may be from apps that you downloaded yourself, but it’s also possible that they’re from spyware that’s been installed without your knowledge.
- Unusual battery drain – Spyware can cause your iPhone to quickly run out of power or drain the battery when you aren’t using it.
- Strange error messages or sudden reboots – This is another symptom of a virus or malware infection on your device.
- Inability to connect to Wi-Fi networks at home or work – A virus or malware infection can prevent you from connecting to Wi-Fi at all, but sometimes it just causes trouble with certain networks.
- Strange text messages -You get a message from someone that looks suspicious and isn’t a contact in your address book. Maybe it says something like “click here to win a free vacation” or “I love you.” The message could also say that you have a virus on your device and need to buy some kind of anti-virus software to remove it.
- Strange emails or texts with attachments – An email or text arrives with an attachment that is supposed to be opened on your iPhone, but doesn’t look right. Or maybe it has no subject or body text at all, just an attachment that looks suspicious or dangerous (like a PDF file).
- Your phone is too hot: If you notice that your device is unusually warm, there may be an issue with one of the apps. Your phone should never get so hot that it feels uncomfortable in your hand or starts to vibrate uncontrollably.
- Your device is jailbroken: Jailbreaking is when users modify their devices so they can install third-party software and use other features not available in the default version of iOS (for example, using an app store other than Apple’s). Jailbreaking can open up security vulnerabilities in an operating system and leave users vulnerable to malware attacks.
- You’re seeing unfamiliar apps: If you start seeing unfamiliar apps pop up in your home screen, consider running an antivirus scan on your device immediately.
➡ Do Chromebooks need antivirus protection?
How do I know if my iPhone has a virus?
Your iPhone doesn’t have a virus, because iPhone viruses don’t exist.
Apple devices are Virus-free, but they can get other types of malware, such as spyware and adware. These malicious programs trick you into installing them by making it seem like they’re something else. For example, they may appear as an app that helps you find new music or games or as an update for your favorite game or app.
Malware is typically installed on your device when you visit a website that has been compromised by hackers who want to steal your personal information. You can help protect yourself by only visiting websites that you know and trust.
Why are there no iPhone viruses?
There are two main reasons why there aren’t any iPhone viruses: Apple’s walled garden approach to the App Store and the iOS security model.
The App Store has strict guidelines on what can be published in it, and apps are reviewed by Apple before they go live in the store. This means that malicious software would have a hard time getting past Apple’s screening process and making it into the App Store.
Apple also uses sandboxing to protect its devices from attack. In this model, each application runs in its own container that cannot access data or resources owned by other applications or processes running on a device — including other apps installed from the App Store.
Reasons Why iPhone is Better than Android
What is a virus?
A computer virus is a piece of software that spreads from one computer to another without the owner’s permission. It does this by attaching itself to a program or document that you download or open on your computer. When it runs, it replicates itself and sends copies to other computers on the network or Internet.
The first known computer virus was created by an English programmer named Fred Cohen in 1986. He called it “Brain” and programmed it to infect Apple II computers running Microsoft’s Disk Operating System (DOS). Brain used DOS as its host environment because DOS was very popular at the time — more than 90% of American businesses ran on DOS-based computers. When someone opened a file containing Brain in their DOS environment, they unwittingly activated it and began spreading it to other computers on their network or through floppy disks.
How good is Bitdefender ? Is Bitdefender safe ?
The most common types of viruses are:
Trojans. These are programs that appear to be useful but actually contain hidden harmful code. Trojans can be disguised as games, apps and other programs, so it’s important to only download apps from trusted sources like the iTunes Store or Google Play Store.
Ransomware. A form of malicious software that restricts access to the device until a ransom is paid. Ransomware can be downloaded automatically when you open an infected email attachment or click on a link in an infected website.
Spyware. Spyware monitors what you do online and sends information back to whoever put it there without your knowledge or permission. Spyware can also record keystrokes, steal passwords and account details, take screenshots of what you do on your phone and send them back to hackers who then use this information for criminal purposes such as identity theft and more serious cybercrimes such as credit card fraud or blackmailing people into paying ransoms in exchange for not sharing their personal information with others.
Is Windows Defender good enough? How good is Windows defender
Where do viruses come from on iOS?
You don’t have to worry about “iPhone viruses.” This is because there is no such thing as an iPhone virus.
There are a number of ways you can get a virus on your iPhone, but they all boil down to one thing: jailbreaking. Jailbreaking removes a lot of the anti-malware features that Apple built into iOS in order to protect users from malicious apps. And since most users don’t know what they’re doing when they jailbreak their devices, it’s easy for them to end up with an infected device.
This doesn’t mean that all jailbreakers will have problems — some people know exactly what they’re doing and are careful about where they get their apps from — but it does make it more likely that something will go wrong if you’ve already opened yourself up for attacks by jailbreaking your device in the first place.
What are the most common ways viruses can get onto your iPhone?
You can download a malicious app from the App Store (or other app marketplace). These apps are designed to steal information or money from you, although they may not be doing so immediately after installation. They may also contain malware that will attack you later on — for example by sending spam messages or making calls at all hours of the day and night.
You can receive a phishing email that contains a link to a malicious website which will try and trick you into logging into your banking details or other sensitive information by pretending it’s an official communication from your bank or government institution.
Sideloading or installing apps from unknown sources — This includes downloading apps from unknown websites or USB drives, as well as installing apps that were not downloaded from the App Store or iTunes Store.
Installing pirated apps — As with above, if an app isn’t legitimately paid for, it could contain malware.
Downloading cracked versions of paid apps — Cracked versions of paid apps are usually infected with malware, so avoid them at all costs!
Wi-Fi connections with weak security. Make sure you always use a secure connection to the internet, like a password-protected Wi-Fi network or a VPN.
Unsecured Wi-Fi networks are one of the biggest risks when it comes to getting infected with a virus on your iPhone or iPad. To avoid this sort of attack, you should always make sure that your Wi-Fi password is strong and unique. A strong password contains at least 10 characters and includes numbers, symbols, and upper- and lowercase letters. For example: $!%^&*()_+|!@#$
➡ Benefits of VPN – Advantages and Pros of Using VPN
If you use public Wi-Fi often or tend to connect to unknown networks then it’s worth investing in a VPN service like NordVPN or CyberGhost Pro where you can connect securely through an encrypted tunnel to the internet. This provides double protection by hiding both your IP address (which identifies you) as well as encrypting all traffic from your device so no one can see what you’re doing online.
➡ How does VPN work? What does a VPN do?
➡ How does VPN work? What does a VPN do?
Ransomware (iOS)
Ransomware is a type of malicious software that blocks access to the target device and demands a ransom to unlock it. Ransomware can be installed through phishing emails or pop-up ads. The most common type of ransomware is Locky, which encrypts files and demands money to decrypt them.
If your device is infected with ransomware, don’t pay the ransom. You won’t get your data back and your device will remain infected, leaving you vulnerable for future attacks. The FBI does not support paying a ransom when dealing with cyber criminals.
If you want to avoid any trouble with this type of malware, then you need to make sure that your operating system is up-to-date at all times so that new security patches are applied whenever they become available. You should also use anti-virus software on all devices because they will often detect such malware before it can do too much damage. If you have already been infected by this type of malware then follow these steps:
Ransomware for iOS devices is rare because most users don’t jailbreak their phones, but it’s possible to get infected with ransomware if you’re using a jailbroken device and visiting a malicious website or app. If you see an alert that says your device has been infected with ransomware, immediately back up your data (if possible), remove the app, then restore your device from backup. If you don’t have access to a backup, take your phone to an Apple Store or other authorized service provider for help.
➡ Protect and Check Your Mac for Viruses and Malware
There are several ways that ransomware can infect your device:
Through email attachments – Ransomware may come in the form of an email attachment such as a Word document or PDF file containing malicious code. These attachments could also be an audio file that plays in your browser when opened. If you open these files on your phone, they may automatically install unwanted apps without your permission.
Through infected websites – Some websites contain code that downloads malware onto your device when you visit them. Once installed, this malware will try to prevent you from using your phone until you pay money through an app store.
Adware (iOS)
Adware is software that displays unwanted advertisements and banners on your screen while you are browsing the web or using apps. Adware may also track your activity and collect personal information such as passwords and credit card numbers.
Advertising-supported software is any program that displays ads on your device without your permission and without paying for them. These programs are usually downloaded from the internet when you install another program or visit a website that advertises itself as free but then asks you to install additional “free” programs before it will work. The most common way this happens is when you download free apps from third party websites rather than directly from the Apple App Store or Google Play store.
➡ Mobile Security: Android vs iOS -Which Is more Secure?
Adware may also contain other types of malware, such as spyware or keyloggers (which capture your keystrokes). This means that adware can collect information about you and send it back to its creator. In some cases, adware can even steal sensitive data like credit card numbers directly from your computer’s memory while it’s running in the background!
There are several different types of adware:
Browser hijackers: These hijackers change your browser settings so that they open up a new tab or window every time you start your web browser. Browser hijackers often display ads when you’re searching for something online — instead of taking you directly to the page that you want, they will redirect you to another page where there are paid search results at the top and organic results below them.
Search engine hijackers: These hijackers replace the default search engine on your device with one they control so that all searches go through their service instead of yours by default.
How to stop it? Remove it?
If your iPhone or iPad is infected with adware, you should remove it immediately. You can do this by uninstalling the app from your device or by contacting Apple support for help removing this infection from your iOS device.
➡ Can someone track my Phone? Even If it is turned off?
Potentially Unwanted Programs (PUP) (iOS)
Potentially Unwanted Programs (PUPs) are software applications that are capable of affecting the performance of a device, but are not considered to be malicious or unwanted. PUPs can include adware, toolbars and other software that users may find annoying or difficult to remove.
There are several types of PUPs:
Bundled PUPs: These types of PUPs come bundled with a program you want to install. For example, if you download and install an app from the App Store or elsewhere on the Internet, there is a chance that Potentially Unwanted Programs may come along with it.
Third-Party PUPs: These types of PUPs are developed by third-party developers who have no affiliation with Apple or any other reputable company. They may be added to your computer without your knowledge through an advertisement banner or pop-up window that appears when you visit certain websites.
Unwanted Toolbars: These types of PUPs appear as extra toolbars on your web browser that may display advertisements and other unwanted content.
What we know about Potentially Unwanted Programs?
- They collect data without your knowledge or consent
- They may display advertisements that are inappropriate for children
- They may alter your browser’s home page setting
- They may change your browser’s default search engine setting
For security reasons, Apple does not allow third party apps to access the operating system. If you want to install an app on your iPhone, you have to go through the App Store.
In some cases, these programs can be used in malicious ways — for example, they could send spam messages or try to trick users into installing additional apps on their devices by displaying ads for them within their interfaces.
While Apple does not recommend using PUPs because of security risks involved, some users may still want them for various reasons.
Spyware (iOS)
Spyware is software that can be used to monitor and record your activity on a mobile device. This includes which websites you visit, the content you view, and the apps you use. Some types of spyware can even record phone calls, texts messages, and other conversations. Spyware is typically installed without the knowledge or consent of the user, but it can also be installed by an individual with access to the device.
The first thing you should do is check if there are any unwanted apps on your phone. To do this, go to Settings> General > iPhone Storage and see if there are any apps with large storage size or low storage space. If so, then delete them right away! If there are no unwanted apps, then you can try resetting your iPhone since this may help remove the malware. But before doing that, make sure that you have backed up your data first and saved all important documents in iCloud Drive (if available).
How to delete apps from an iPhone or iPad.
How to delete apps on iPhone 11, 12, X
Delete the offending app: Remove any apps that are causing problems with your device. To do this, open the “Settings” app and select “General,” then “Privacy.” From there, scroll down until you see “Contacts,” “Calendars,” “Call History” or any other app that looks unfamiliar to you. If there are any apps listed here that look suspicious or unfamiliar to you — for example if they have names like “MobileSafari” instead of Safari — tap on them one by one and then tap on “Delete App” at the bottom of each screen.
iPhone virus threats – the facts
The iPhone is a very popular device, and it’s no surprise that malicious hackers would want to target it.
The iPhone is a popular smartphone that has been around for a few years now, and is the most popular smartphone in the world. Many iPhone users are now asking whether there are any iPhone viruses.
The answer is no. There are no known viruses targeting iOS devices (iPhone, iPad etc.) as of yet.
The good news is that you can protect yourself from these threats. Here are some tips:
Don’t click on unknown links or attachments in emails or messages. You should be wary of links and attachments even if they come from someone you know, as they could have been compromised by viruses or other malicious software (malware). Also be careful about opening emails that contain links to webpages that are not secure, as these may contain malware.
Install anti-virus software on your computer and keep it up to date with the latest virus definitions. This will help protect your computer against viruses, which can spread through networks and devices connected to them. Some antivirus applications include features that scan for known malware and stop it from installing itself on your device.
If you’re unsure about an email or a message asking for personal information such as passwords or credit card details, contact the sender directly using another method (such as phone) before responding. If they don’t respond via another method, it’s likely they’re not who they claim to be and you should delete their message without replying.
Why are there so few iPhone viruses?
Apple’s iOS operating system is one of the most secure and stable mobile platforms in existence. The majority of users don’t even have to think about security, as there are few threats to worry about.
There are several reasons why there aren’t many iPhone viruses:
The iPhone is not as popular as Windows computers. This means there aren’t as many people who would find an iPhone virus useful.
The iPhone doesn’t have a lot of users compared to PCs. The bigger the audience of users, the easier it is for a hacker to make money off of attacking them with malicious software.
Hackers have many other options for attacking devices besides iPhones (like PCs). While it’s possible that someone will develop an iPhone virus someday, it’s not likely that they’ll do so anytime soon because there are plenty of other ways to make money through hacking without going after Apple products — most notably PCs and Android phones.
The main reason is that Apple has made it difficult for malicious software to run on its devices. This is because developers must go through strict checks before they can write apps for the App Store — and even then, the apps need to be approved by Apple before they can be downloaded.
But there are other reasons too. For instance, iPhones aren’t as vulnerable as Android phones because they aren’t used as much by businesses or governments. This makes them less attractive targets for hackers looking to steal or destroy data.
What can malware do to your device?
Malware can be used to access your device, steal data from your device and even spy on you.
A malware infection could be used for:
Spying: Malware can spy on you by recording what you type and sending it to a remote server.
Data theft: Malware can collect your personal information and send it to a remote server.
Device access: Malware can take control of your device and do anything it wants with it.
Installing itself as an app on your device.
Hijacking your browser so that it displays ads instead of the content you requested.
Changing settings on your device without your knowledge or permission, such as changing the default search engine or home page on your browser.
Stealing your personal information, such as passwords or credit card numbers.
Opening up a backdoor into your device so that other types of malware can gain access to it later.
Malware is short for malicious software. It’s a program designed to disrupt computer operation, gather sensitive information, or gain access to private computer systems. Malware includes computer viruses, worms, Trojan horses, and other malicious programs. A virus is a type of malware that can replicate itself. Worms and Trojan horses are self-contained executable files that spread from one computer to another over a network.
Malware can be very destructive, but it also can be used for legitimate purposes. For example, anti-virus programs use malware to scan for and remove malicious software from computers. Malware can become a problem if your device becomes infected with it — either accidentally or intentionally through malicious intent.
The most common way people get infected with malware is by clicking on links in email messages or visiting websites containing malicious code (malicious software). You might not notice anything unusual at first when this happens because the malware may not do anything immediately after it infects your device. Instead, it could be lurking in the background until it’s ready to take action so that you won’t suspect anything unusual going on with your device until it’s too late and the damage has been done.
How can I prevent this happening to me?
You should always update your operating system, browser and apps so that you have the latest security fixes installed. A good antivirus program will protect your device from malicious software that might try to infect it. If possible, keep your phone’s data encrypted with a password or biometric authentication. This will prevent others from accessing the sensitive information on your device if it is stolen or lost.
The first thing to do is check your security software. Many antivirus programs will have alerts that let you know when they have detected a virus. If you see this message, then you know that something is wrong with your computer.
If your iPhone has been infected by a virus and the antivirus software didn’t catch it, then it’s time to take action. How can I prevent this happening to me? The best way is to always be careful about what you download from the internet and follow these rules:
Don’t open email attachments unless you know who sent them and why they sent them. Do not click on links in email messages unless you know where they lead (and even then, only click on links from people or organizations that you trust). Don’t download and install software from websites that aren’t well known or reputable. If an application installs itself without asking for permission first, don’t use it!
If a message pops up, what should I do?
If you are using a iPhone and see a pop-up window that says “Your iPhone has been infected by a virus,” or something similar, do not click on it!
This is an attempt to trick you into clicking on the link that is included in the message. If you click on this link, it will download malicious software onto your computer. This can cause your computer to crash or run slowly, or it could allow hackers access to your personal information.
- Do not open any links that are sent to you via SMS or email and do not install any apps from unknown sources.
- Always check the permissions required by an app before installing it on your device. If an app asks for too many permissions (such as access to contacts or location), then it is more likely that this app contains a virus.
Should I get anti-virus software for my iPhone?
The short answer is yes. The longer answer is that the built-in security features in your iPhone are designed to protect against most common threats. But if you want an extra layer of protection for your device, there are a number of good options.
Apple’s built-in security features
If you haven’t yet done so, you’ll want to enable two features: iCloud backup and Find My iPhone. Both of these features are enabled by default when you set up your device; if they’re not enabled, go to Settings > iCloud > Backup and tap the toggle next to iCloud Backup. Then go back one level (to Settings) and tap Find My iPhone; tap the toggle next to Find My iPhone on this screen as well.
You’ll also want to make sure that your device is set up with a passcode lock — go to Settings > General > Passcode Lock and enter a passcode that meets the requirements specified here (e.g., at least six digits long).
Anti-virus apps for iOS devices
There are several anti-virus apps available for iOS devices; we’ve tested five of them below: Avast AntiVirus FREE Security, Bitdefender Mobile Security, Norton 360 & Avira Mobile Security
While it is unlikely you will get a virus on your iPhone, it is important to be aware of potential threats.
While it is unlikely you will get a virus on your iPhone, it is important to be aware of potential threats.
The most common type of malware, or malicious software, that can infect an iPhone is known as a SMS worm. This type of virus spreads by sending copies of itself to other mobile phones via text messaging. The worm’s payload can be anything from an annoying message or graphic to a malicious program that steals information from the phone’s address book or contacts list.
There are several ways to combat SMS worms:
Don’t open text messages sent from unknown senders. For example, if you receive a message containing a “virus alert,” don’t open it; instead, delete it immediately.
Avoid replying to text messages with sensitive information like credit card numbers and passwords unless you are sure the message is legitimate. If you’re not sure whether an email or text contains malicious code, contact your service provider or Internet security company for help before opening it.
Use antivirus software that scans for malware and viruses on your computer and mobile device. Look for an antivirus program that also protects against spyware.
Do not click on links in emails or text messages from people you don’t know very well or at all.
Make sure that the websites you visit are secure by looking for “https” instead of “http” in the web address bar (the ‘s’ stands for secure).
Be cautious when downloading free apps from unknown sources or trusted developers who have been hacked. Keep an eye out for apps that have a higher than usual number of reviews or ratings because they may contain harmful code designed to infect devices with malware.
Ransomware can block the use of a device or a person’s files until a ransom is paid.
Ransomware can block the use of a device or a person’s files until a ransom is paid. This type of attack may also be called cryptovirus, cryptotrojan, crypto-ransomware or ransomware.
A ransomware attack is when a hacker uses software to lock up your computer and then demand payment in exchange for the unlocking code. The most common way to do this is by encrypting your files — making them unreadable — and demanding payments in order to decrypt them.
Ransomware attacks are typically carried out by email spamming (sending unsolicited emails), but they can also be delivered through malicious downloads.
Some ransomware attacks require you to pay in Bitcoin, which makes it difficult for law enforcement agencies to track down the perpetrators behind these crimes.
The Chthonic virus is a ransomware program that was first discovered in November 2016. It has since been updated, and the newest version, which has been detected since March 2017, is known as AceDeceiver.
Ransomware can block the use of a device or a person’s files until a ransom is paid. In the case of Chthonic, the malware blocks victims’ access to their devices until they pay $300 in Bitcoin. The ransom must be paid within three days or it doubles to $600.
Ransomware can block the use of a device or a person’s files until a ransom is paid. Ransomware is typically installed through phishing emails and malicious websites. Once it’s on your device, ransomware may be able to collect personal information.
Ransomware often arrives in an email attachment or as a link in an email message. The attachment might be disguised as something else, like a PDF file or photo. If you open it, the ransomware will start running immediately and begin encrypting files on your hard drive.
When ransomware infects your device, it usually changes some settings on your computer so that it can continue running after you turn off your computer or restart it. It might change the background image or try to disable anti-virus software so that it can continue running undetected.
Ransomware often targets people who use online banking services, since criminals hope that users will pay up rather than risk losing financial records or other sensitive information stored on their computers.
Be wary of suspicious emails and attachments that contain malware.
Many people still fall for the scam, so it’s worth taking a look at how the latest iPhone virus works.
The email contains a link to a website that looks real enough. It looks like an Apple site, but it’s not. It could be from someone you know or from someone you don’t know. The email may say: “I can’t believe this is happening!” or “Check out this video.”
The link takes you to a site where you are asked to install an app to watch the video — but this app is actually malware that will infect your phone. When you click on the button, it downloads malicious software onto your device, which then enables hackers to remotely control it and steal personal data. Once they have control of your phone, they can read all of your emails, contacts and text messages; see what websites you’ve been visiting; record everything you type on the keyboard (including passwords); collect photos stored on your phone; access email accounts; and send messages while pretending to be you — even sending spam emails from your account!
Be wary of suspicious emails and attachments that contain malware. If you receive an email with an attachment asking for personal information, don’t open it. If you receive an email with a link that directs you to a website that looks like a legitimate site but isn’t, don’t click on the link. Instead, go directly to the real website by typing its address into your browser’s address bar.
Be careful about what you share on social media sites such as Facebook or Twitter. You never know who might be lurking around these sites waiting for something to grab their attention — such as your personal information or photos — so don’t post anything that could be embarrassing or damaging if it fell into the wrong hands.
Never download pirated software or illegal music and movies through file sharing sites because they often include malware that can harm your device and cause financial loss when used in conjunction with credit card numbers stolen from other users’ devices.